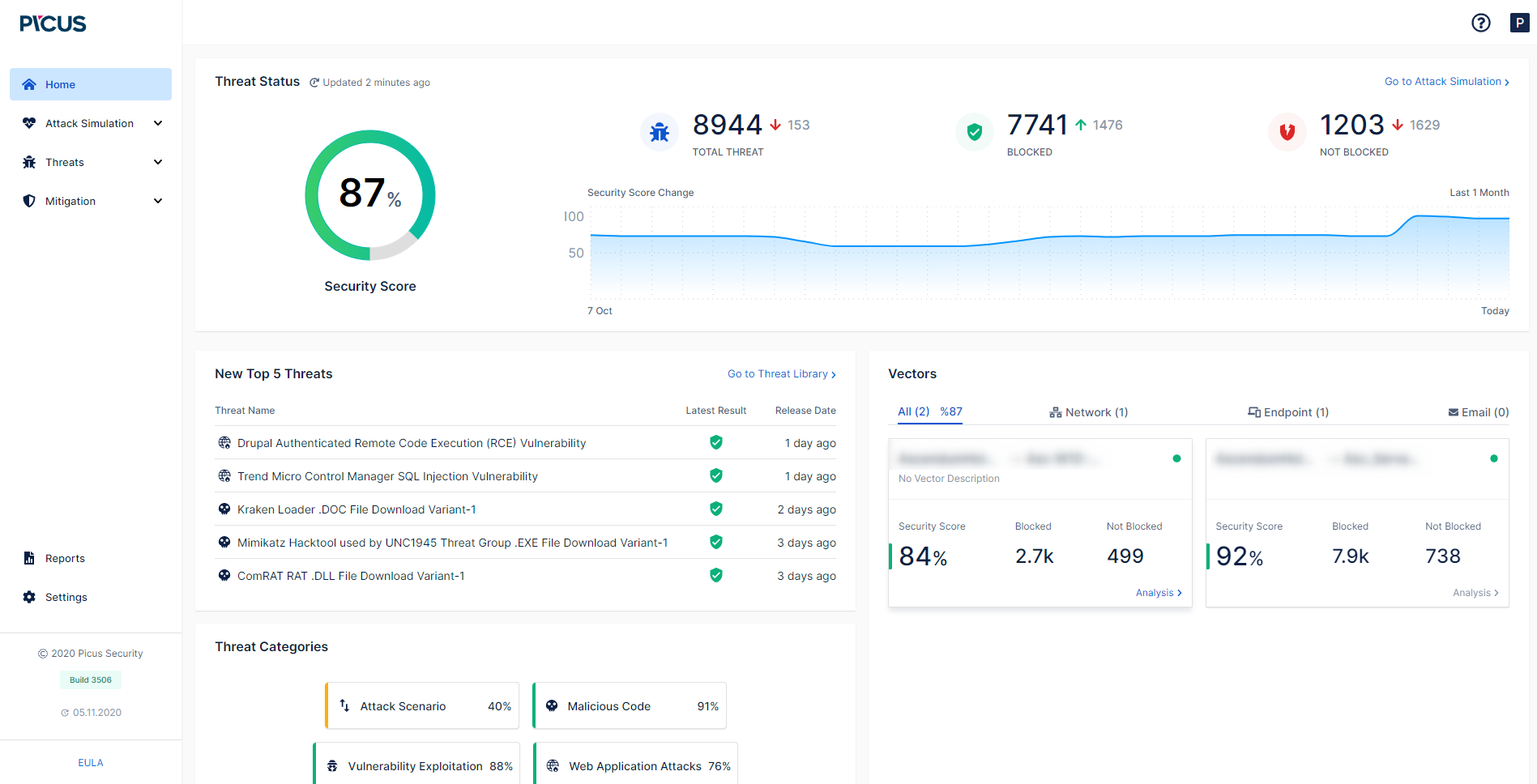
First Step in Cyber Threat Preparedness
Before cybercriminals, simulate your security technologies 7x24 with real threat scenarios, analyze the gaps in your security structures.
DemirBT is the MSP partner of Picus Security.