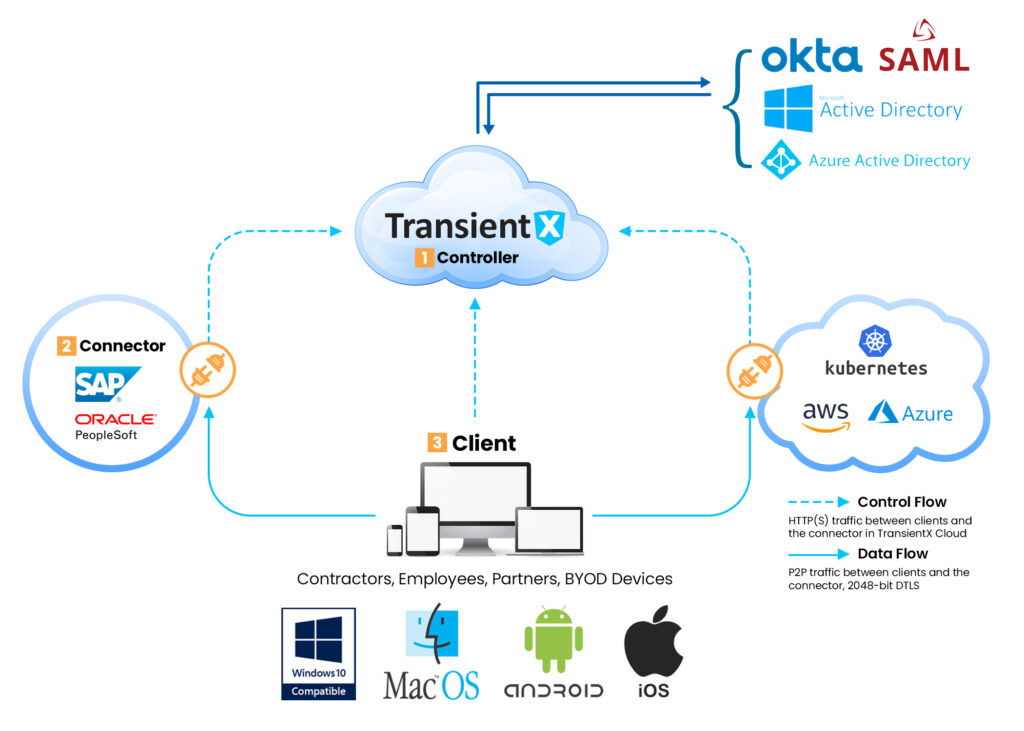
How Does TransientX Work?
1. Control Unit: It is the component that verifies, allows and regulates connections.
The Control Unit is provided as a service in the TransientX cloud (SaaS).
2. Connector: Connectors are located in front of applications to be accessed, usually
in a private cloud or on-premises data center.
3. Clients: Users upload to their devices to access corporate resources. When an authenticated
user requests access to a remote institution resource, a temporary application network is created between the user's
device and the institution resource (enterprise application, server, etc.). The connectors are never exposed to the internet,
and there is no external connection request to these connectors. Thus, they are located behind the firewall and other security
elements. A peer-to-peer tunnel is established between the application on the user device and the connector, which does not allow
data traffic to pass through cloud gateways. Traffic is done end-to-end over DTLS protocol with 2048 bit switches. TransientAccess
combines a zero-trust network architecture with granular access control policies, application segmentation and full visible audit logs.